
Healthcare workflows have moved online—from intake packets and payment policies to informed consents and telehealth authorizations. The natural question for any clinic leader is: are patient digital contracts legally valid in the U.S.? In short, yes—provided your process aligns with federal and state e-signature laws, evidentiary standards, HIPAA privacy/security expectations, and any specialty-specific rules (e.g., controlled substances, research, or state consent statutes).
This guide explains the legal bedrock (ESIGN/UETA/ESRA), clarifies electronic vs. digital signatures, and details how to implement an auditable, clinic-friendly process. You’ll also see where Ninsaúde Sign fits in to make all of this operationally simple.
Before we continue, we need to ask: Are you already familiar with Ninsaúde Clinic? Ninsaúde Clinic is a medical software with an agile and complete schedule, electronic medical records with legal validity, teleconsultation, financial control and much more. Schedule a demonstration or try Ninsaúde Clinic right now!

Legal foundation: ESIGN, UETA, and New York’s ESRA
The ESIGN Act (2000) establishes that a contract or signature may not be denied legal effect solely because it is electronic. Most states also adopted UETA, which harmonizes state law so that electronic records and signatures satisfy “writing” and “signature” requirements when parties consent to transact electronically. New York did not adopt UETA but enacted ESRA, which similarly recognizes e-signatures for most transactions, subject to limited exceptions.
For clinics, this means admissions agreements, financial policies, no-show terms, arbitration clauses, and informed consents can be executed electronically—as long as you capture consent to use electronic means and maintain adequate proof of identity, intent, and document integrity.

HIPAA alignment: privacy, security, and vendor management
HIPAA does not ban e-signatures. What it requires is appropriate protection for PHI (access controls, encryption in transit and at rest, audit trails) and Business Associate Agreements (BAAs) with vendors that store or process PHI. Your e-signature workflow should slot into your HIPAA Security Rule program: risk analysis, role-based access, least privilege, contingency planning, and incident response.
Practical guardrails:
- Use unique patient links with expiration and optional two-factor authentication (2FA/OTP) for remote signing.
- Maintain tamper-evident PDFs with a document hash, timestamp, and complete audit trail (IP, user agent, events like sent/viewed/signed).
- Implement retention schedules that match legal and payer requirements; lock down deletion permissions.
- Execute a BAA with the e-signature vendor and confirm encryption/hosting posture.
Electronic vs. digital (PKI) signatures—what clinics actually need
- Digital signatures (PKI/certificate-based): cryptographically bind identity and content; often used when regulations demand higher assurance (e.g., DEA EPCS for controlled substances e-prescribing).
- Electronic signatures (typed name, click-to-sign, draw-to-sign): widely valid if supported by evidence of identity, intent, and integrity. For patient contracts and informed consents, an auditable electronic signature is typically sufficient unless a statute or payer policy requires a higher-assurance method.
Takeaway: Match the assurance level to the document risk. Reserve PKI where mandated; use robust electronic signatures with strong evidence for everything else.

Informed consent, telehealth, and specialty nuances
Electronic consent is valid when patients receive clear, understandable information (risks, benefits, alternatives) and have an opportunity to ask questions. For telehealth, include modality limits, emergency instructions, data handling, recording policy (if any), and out-of-state considerations.
Edge cases to consider:
- Minors: ensure the correct legal representative signs; capture relationships (parent/guardian) and, where relevant, assent from mature minors.
- Language access: provide plain-language versions; offer translations and qualified interpreter workflows when needed.
- Accessibility: ADA expectations favor documents readable by screen readers and interfaces navigable via keyboard; ensure font size, contrast, and alternative text for assistive tech.
- Research: if the consent is part of a study, align with IRB requirements and FDA e-consent guidance.
Identity, intent, and integrity: building courtroom-ready evidence
Courts and payers care about who signed, what they agreed to, and whether the record is trustworthy. A defensible stack includes:
- Identity proofing proportional to risk: verified email/phone, knowledge-based checks, OTP/2FA, and optional ID capture in higher-risk scenarios.
- Intent capture: explicit “I agree/I consent” actions, initialing key clauses, and confirmation screens before submission.
- Integrity: tamper-evident PDFs, hashing, time-stamps (with synchronized clock), locked versioning, and full audit trails.
- Context: store the exact document version shown to the patient, any linked materials (pre-op instructions, disclosures), and staff notes in the EHR.
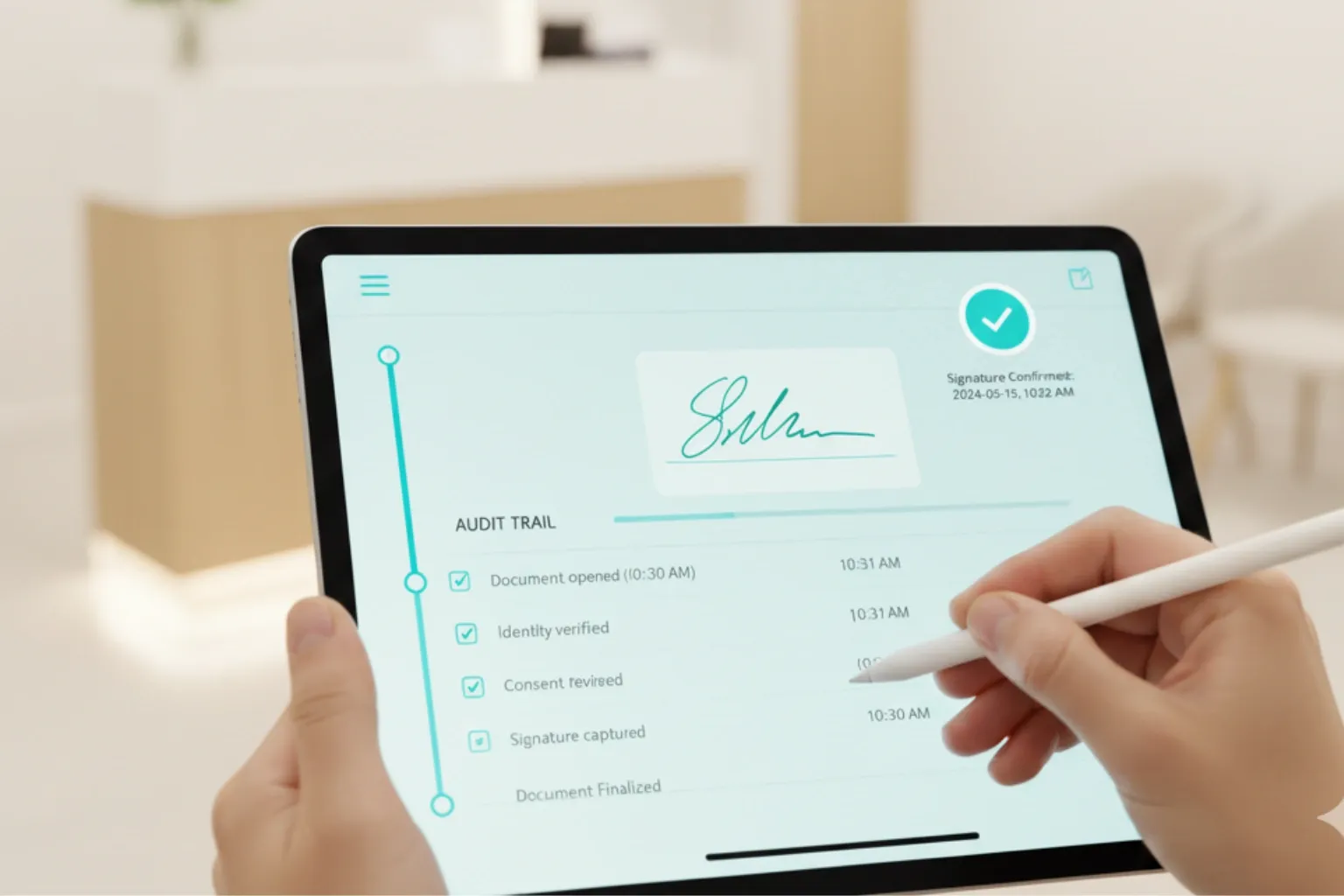
Medicare/Medicaid and payer audits
Payers increasingly accept e-signatures, but your policy documentation matters. Maintain a written e-signature policy describing identity verification, audit logging, retention, and exception handling. For audits, be ready to export: the signed PDF, the audit trail, the presented document version, and any related communications (reminders, confirmations). Align retention with federal/state and payer rules (often 6–10+ years, depending on record type and state).
Record retention, e-discovery, and litigation readiness
Adopt a retention schedule with legal input, and pair it with defensible legal hold procedures for potential litigation. Store documents in a system that supports:
- Immutable or write-once storage options for critical agreements;
- Granular access controls and detailed access logs;
- Export at scale for discovery;
- Disaster recovery objectives (RPO/RTO) that meet your risk tolerance.
Notarization and witnessing (when required)
Most patient contracts do not require notarization; however, certain documents (estate/POA, specific state forms) might. If notarization is needed, consider remote online notarization (RON) where permitted. If witnesses are required, configure multi-signer workflows that record each participant’s identity, role, and timestamp.

Common pitfalls—and how to avoid them
- Version drift: patients sign an outdated template.
- Fix: single source of truth, template ownership, and automatic version lock on sign.
- Weak identity checks for high-risk actions.
- Fix: step up to 2FA or ID validation when risk increases (e.g., high-value financial agreements).
- Over-collection of PHI in contracts.
- Fix: apply minimum necessary; move clinical details to the EHR.
- Unclear language that undermines consent.
- Fix: plain-language review; staff training to invite questions.
- Vendor gaps (no BAA, unclear data locations).
- Fix: BAA, security due diligence, data residency clarity, and routine audits.
Implementation roadmap (quick start for clinics)
Week 1
- Map document types (admissions, financial, no-show, arbitration, informed consent, telehealth).
- Classify assurance levels (electronic vs. digital/PKI only where required).
- Approve templates legally and simplify language; define retention.
Week 2
4) Configure e-signature flows: identity steps, signer order, required fields, and reminders.
5) Integrate with the EHR so signed PDFs return automatically to the patient chart.
6) Train front desk and clinical teams; publish a short internal SOP.
Ongoing
7) Quarterly audits of samples for evidence completeness; update templates and access roles as needed.
Where Ninsaúde Sign fits (hands-on)
- Electronic signatures with visible marks on PDFs and a complete audit trail (timestamps, IP, user agent, event history).
- Automatic round-trip: once signed, the document returns to the patient record in Ninsaúde Clinic, and a copy is sent to the clinic’s system email for internal compliance.
- Template library for informed consent, telehealth, media authorization, and financial agreements—customizable by specialty/unit.
- Open API for advanced automations (conditional sends, reminders, BI exports).
- Works alongside digital (PKI) signature workflows used elsewhere in Ninsaúde (e.g., for prescriptions), keeping the right assurance level for each document type.

U.S. compliance checklist (copy/paste)
- ✅ ESIGN/UETA/ESRA mapped; consent to e-transactions captured.
- ✅ HIPAA risk analysis done; BAA in place with e-signature vendor.
- ✅ Identity controls proportional to risk (OTP/2FA when appropriate).
- ✅ Tamper-evident PDFs, hash, timestamps, and full audit trail stored.
- ✅ Role-based access, retention policy, and disaster recovery tested.
- ✅ DEA EPCS handled separately in certified software (if prescribing controlled substances).
- ✅ Accessibility and language-access accommodations documented.
- ✅ Quarterly sampling/audits for compliance and quality.
Important note
This article is for informational purposes and does not constitute legal advice. State-level nuances (e.g., witness/notary requirements, arbitration enforceability, specific consent rules) may apply. Consult counsel to calibrate your policy and templates.
Did you like this information? Then get ready for a continuous learning journey by following our blog. Are you a healthcare professional and don’t yet know the benefits of Ninsaúde Clinic? Stay ahead, optimize your processes, and raise the standard of patient care!

